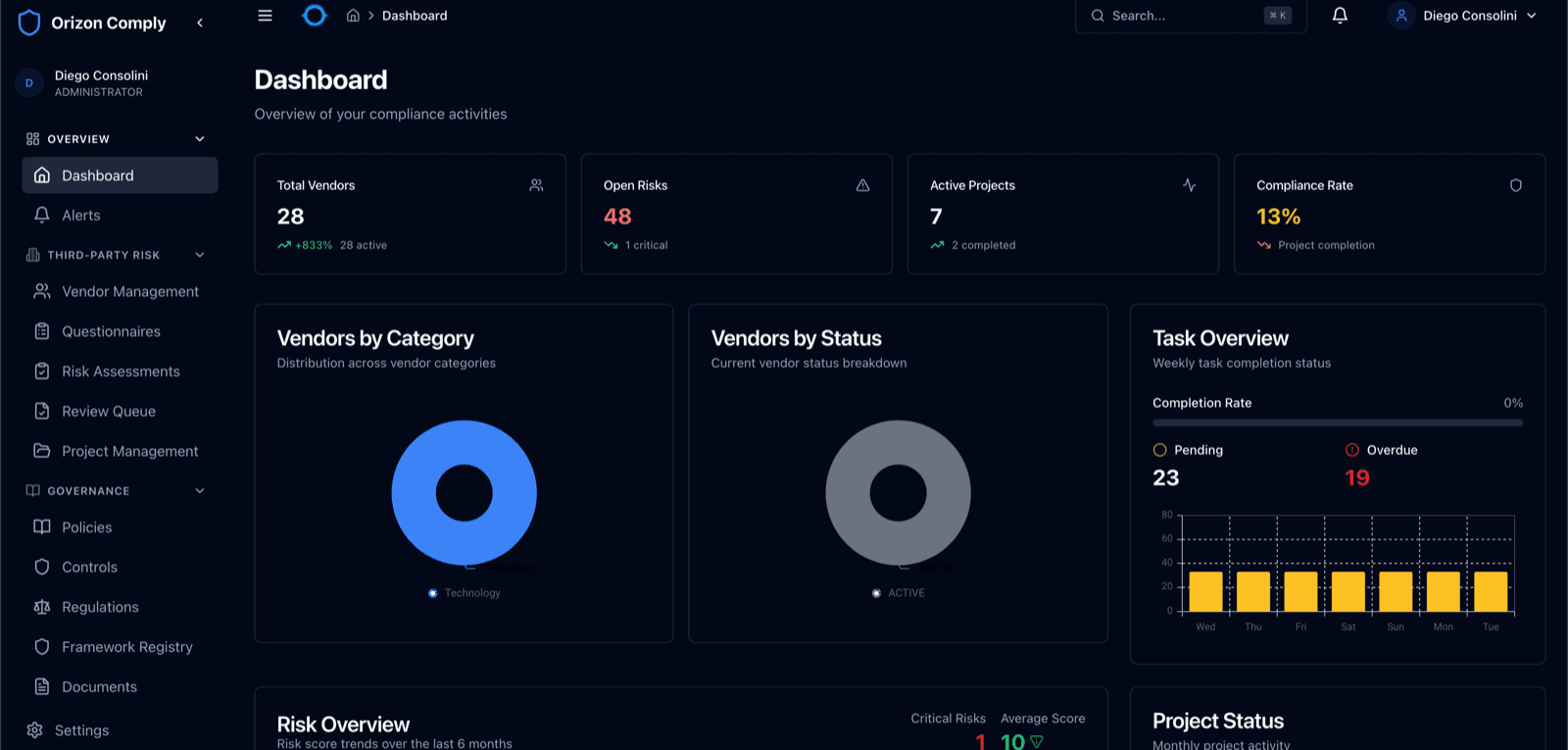
One platform for third-party risk management, regulation tracking, controls mapping, and AI-powered compliance auditing. Built for security teams that need verifiable outcomes.
Track regulations at article level, manage controls across frameworks, and generate compliance evidence — all in one registry.
Manage the full vendor lifecycle from onboarding to assessment. Vendors complete questionnaires via a secure portal — no internal system access required.
Run AI-powered compliance audits without sending a single byte to external services. All processing happens locally using open-source models.
Manage the full vendor lifecycle — from onboarding and risk classification to assessment and continuous monitoring. Vendors complete questionnaires through a secure portal without ever accessing your internal systems.
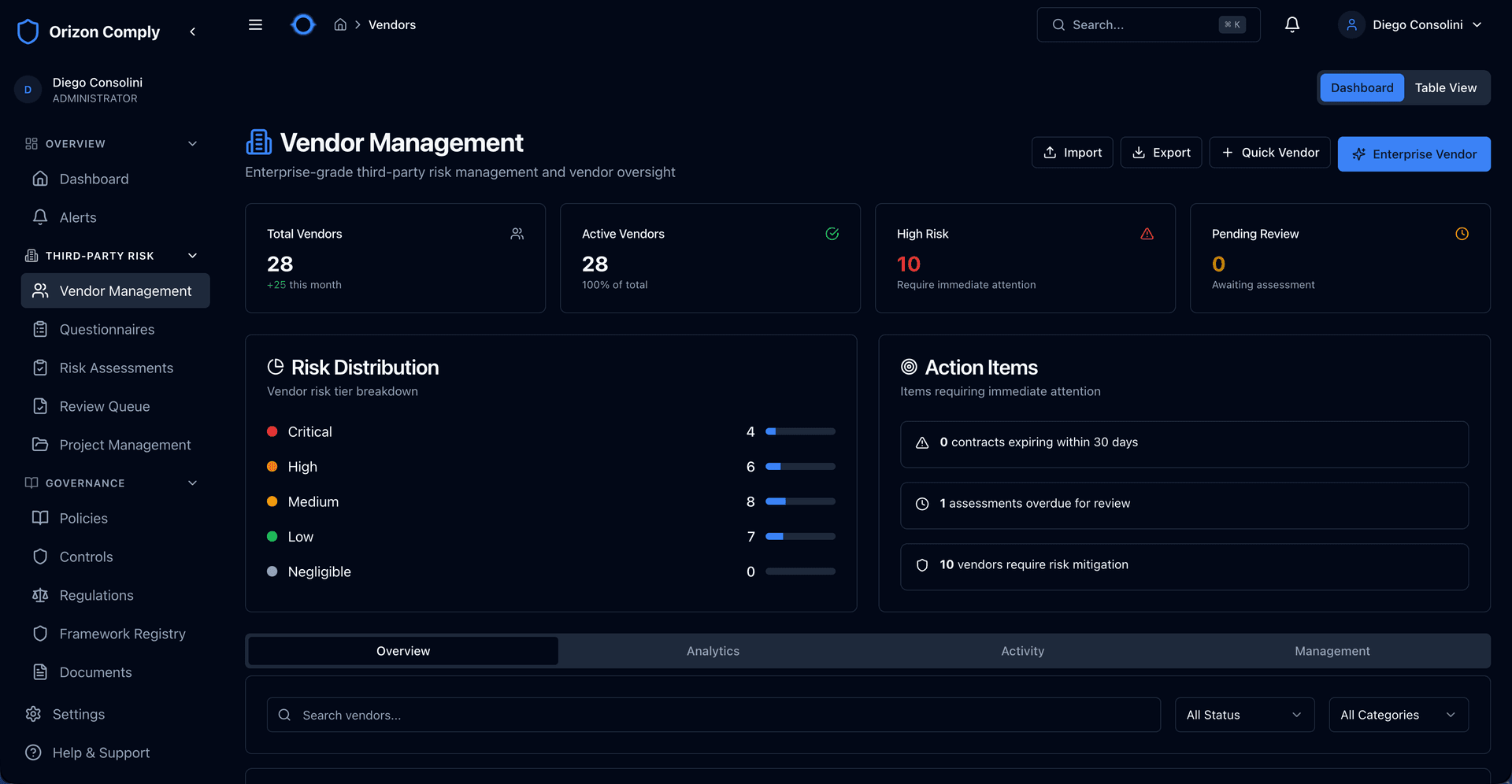
Real-time view of your vendor portfolio with 5-tier risk distribution, action items requiring attention, and import/export capabilities for bulk operations.
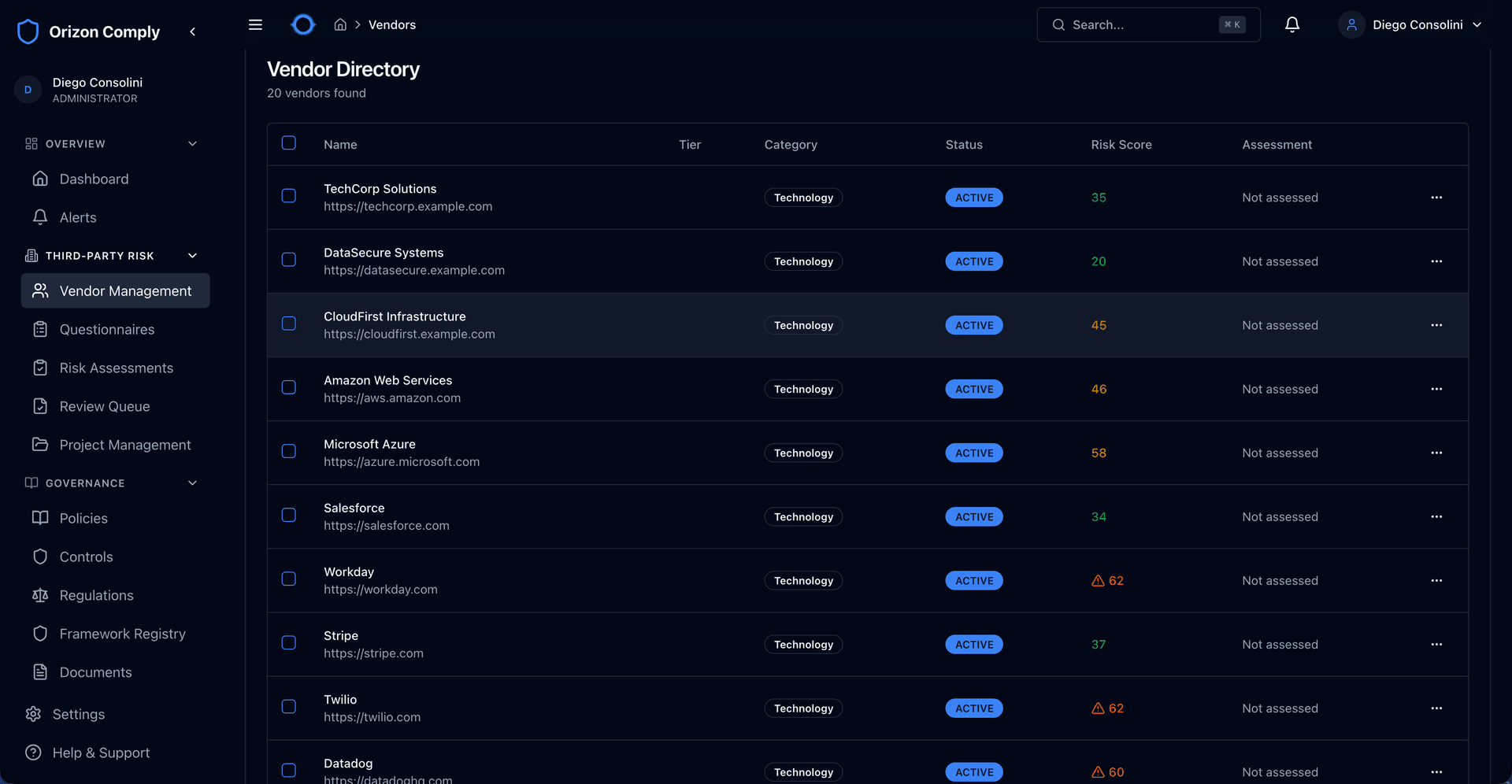
Searchable directory tracking risk scores, assessment status, and vendor categories. Filter by tier, status, or category to focus on what matters.
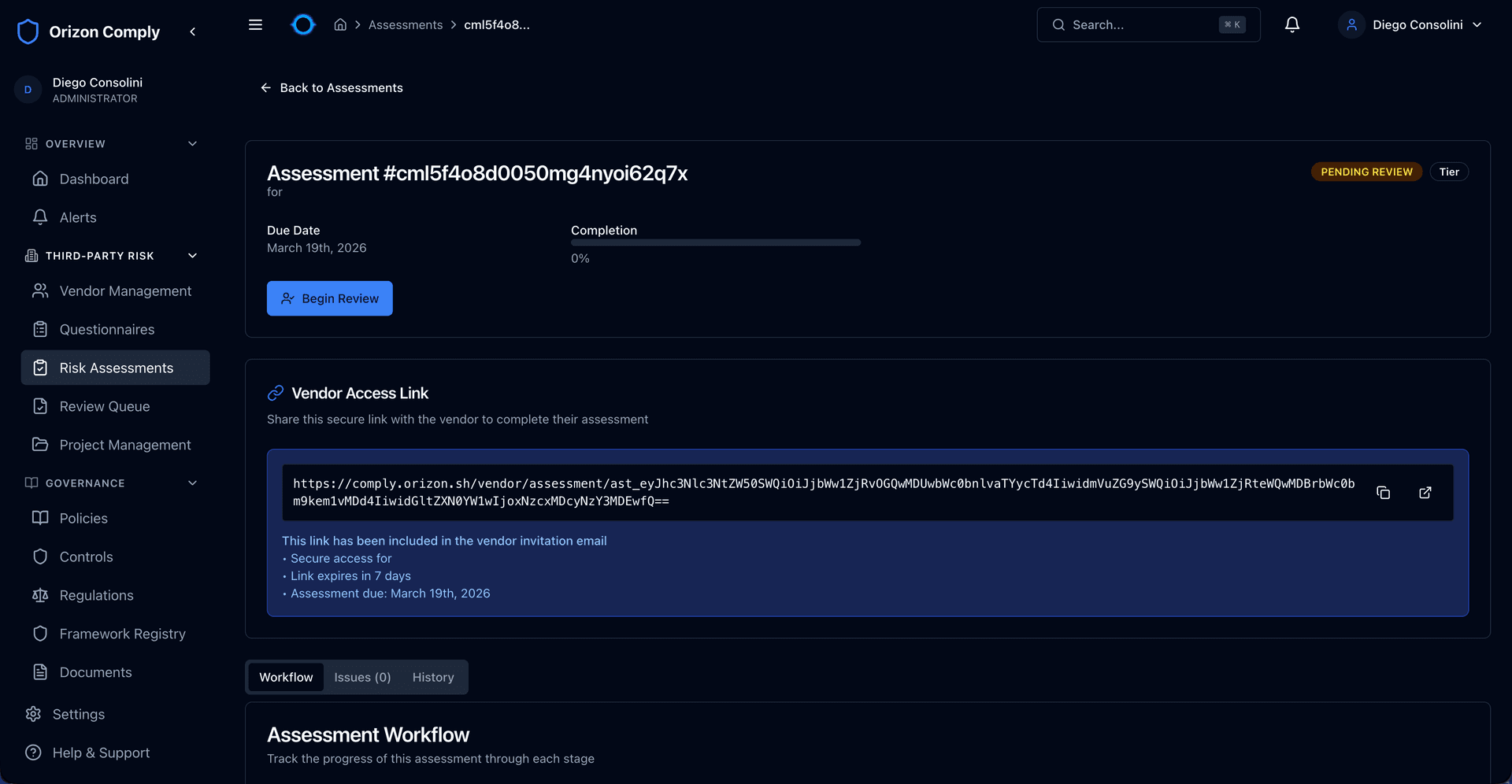
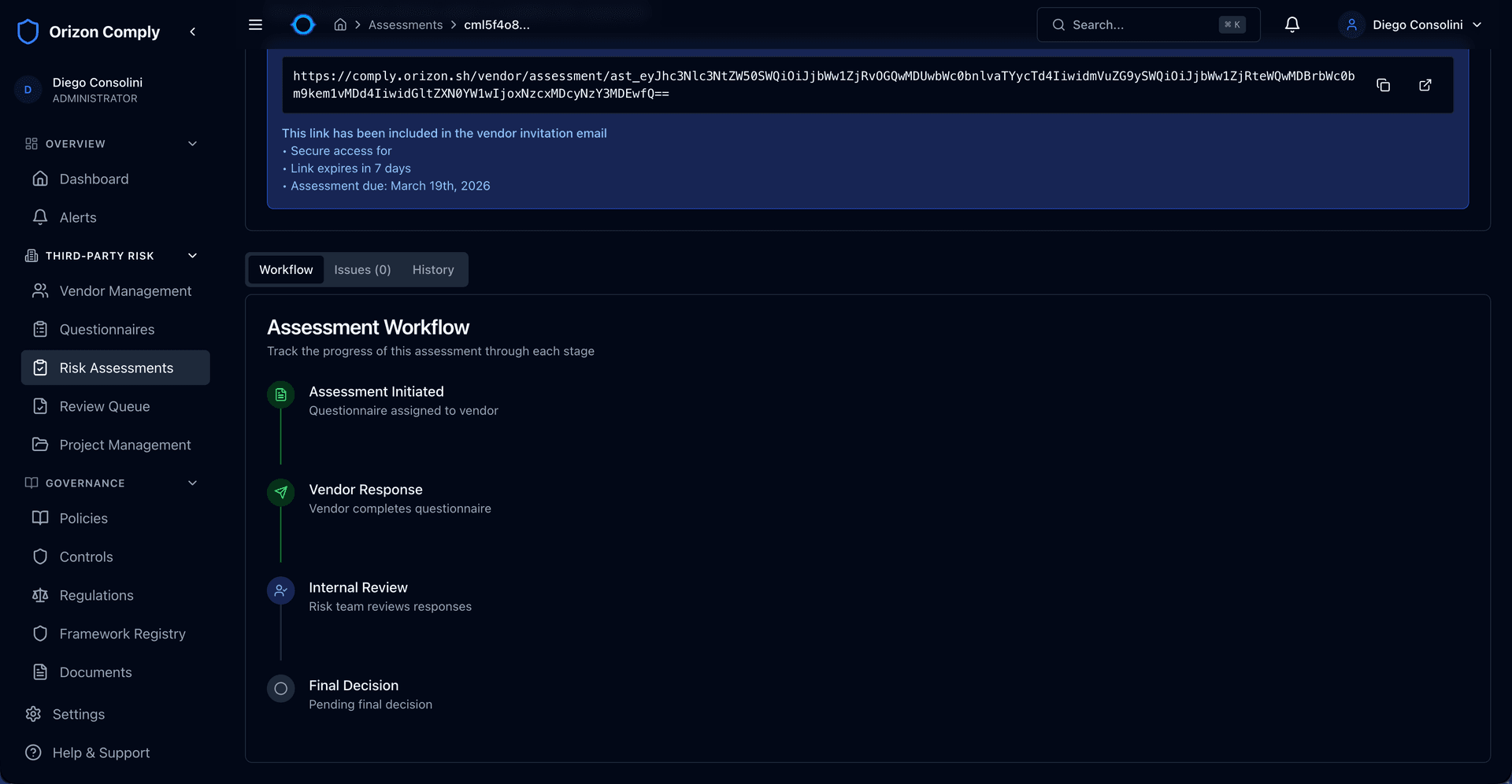
Vendors receive a secure link with a cryptographic token — no account creation needed. The full workflow runs from invite through response, internal review, and final decision with a complete audit trail at every stage.
Identify, assess, and track risks across your organisation with an interactive heatmap and structured scoring. Probability-by-impact analysis with residual risk tracking gives your board a clear picture of exposure.
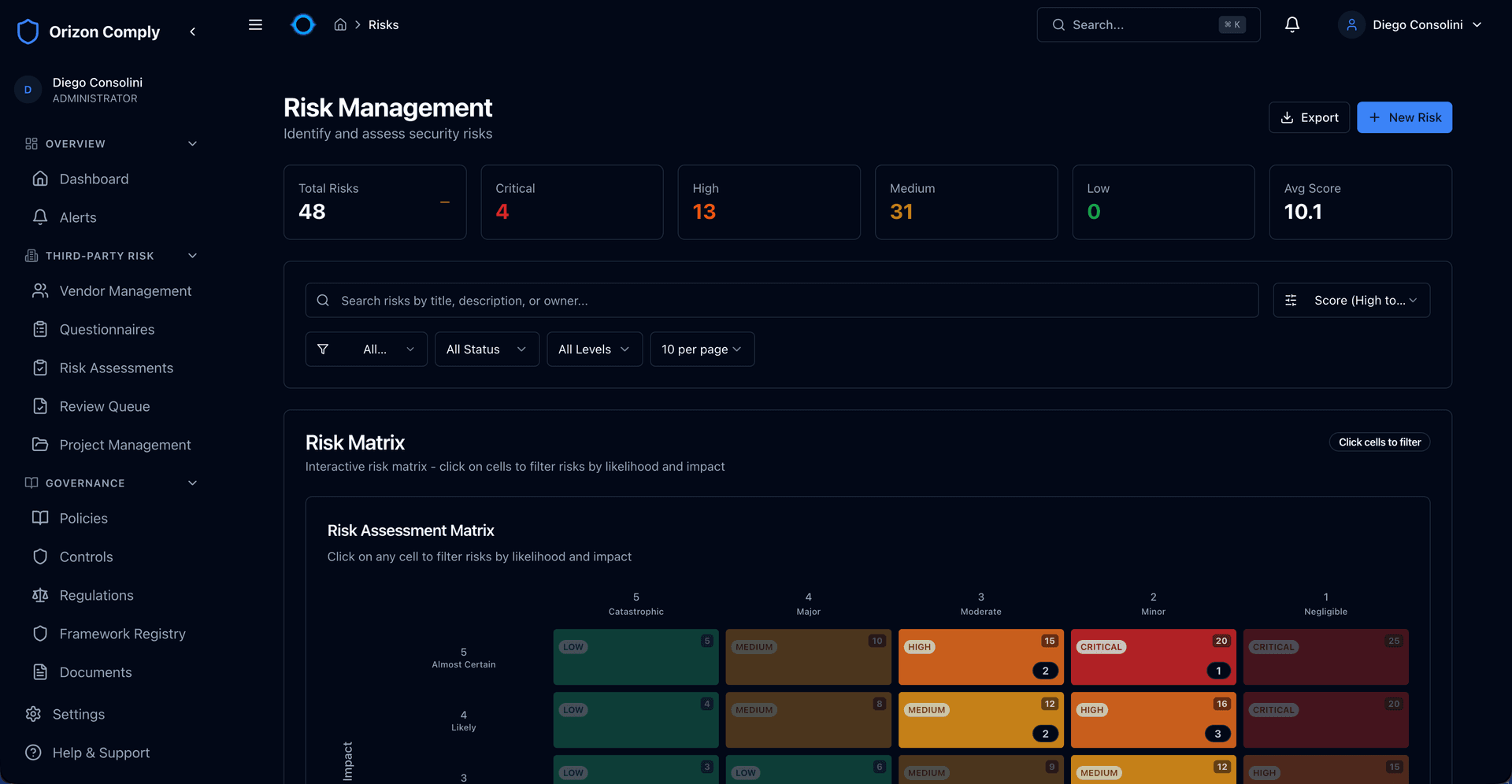
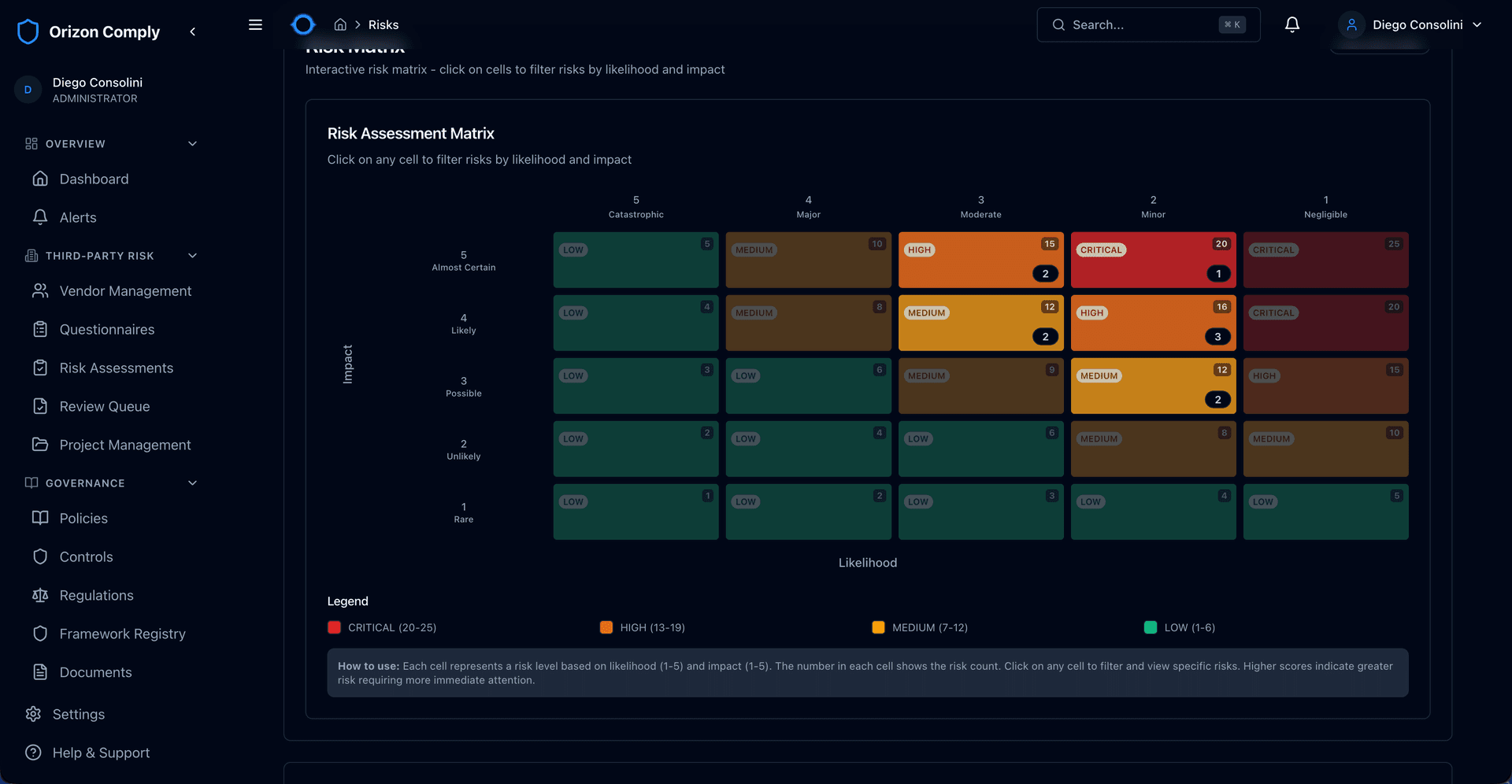
Track regulations at article level, manage controls across frameworks, and map requirements to your vendor portfolio. Every framework is built in — not bolted on.
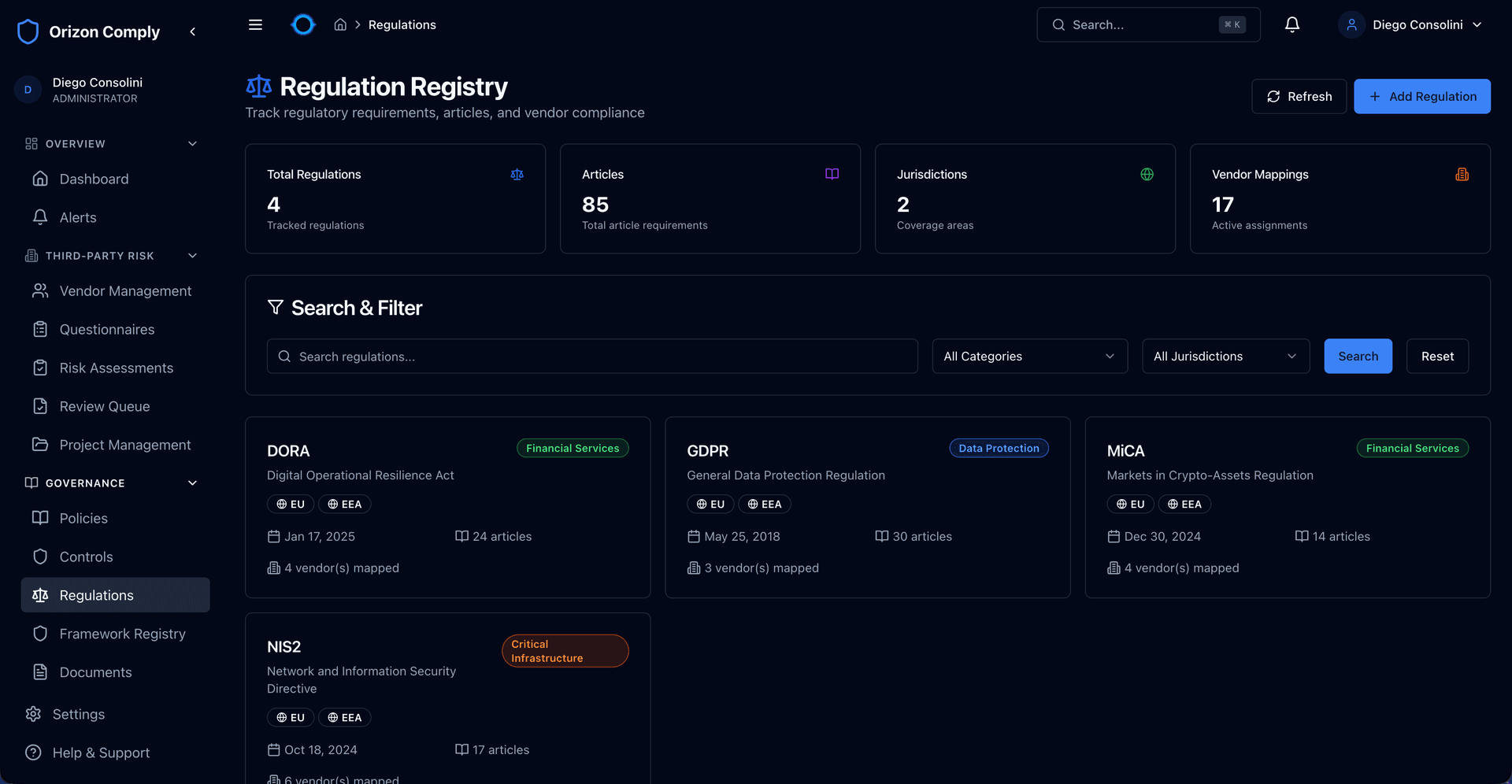
Regulation Registry — article-level tracking with vendor mapping
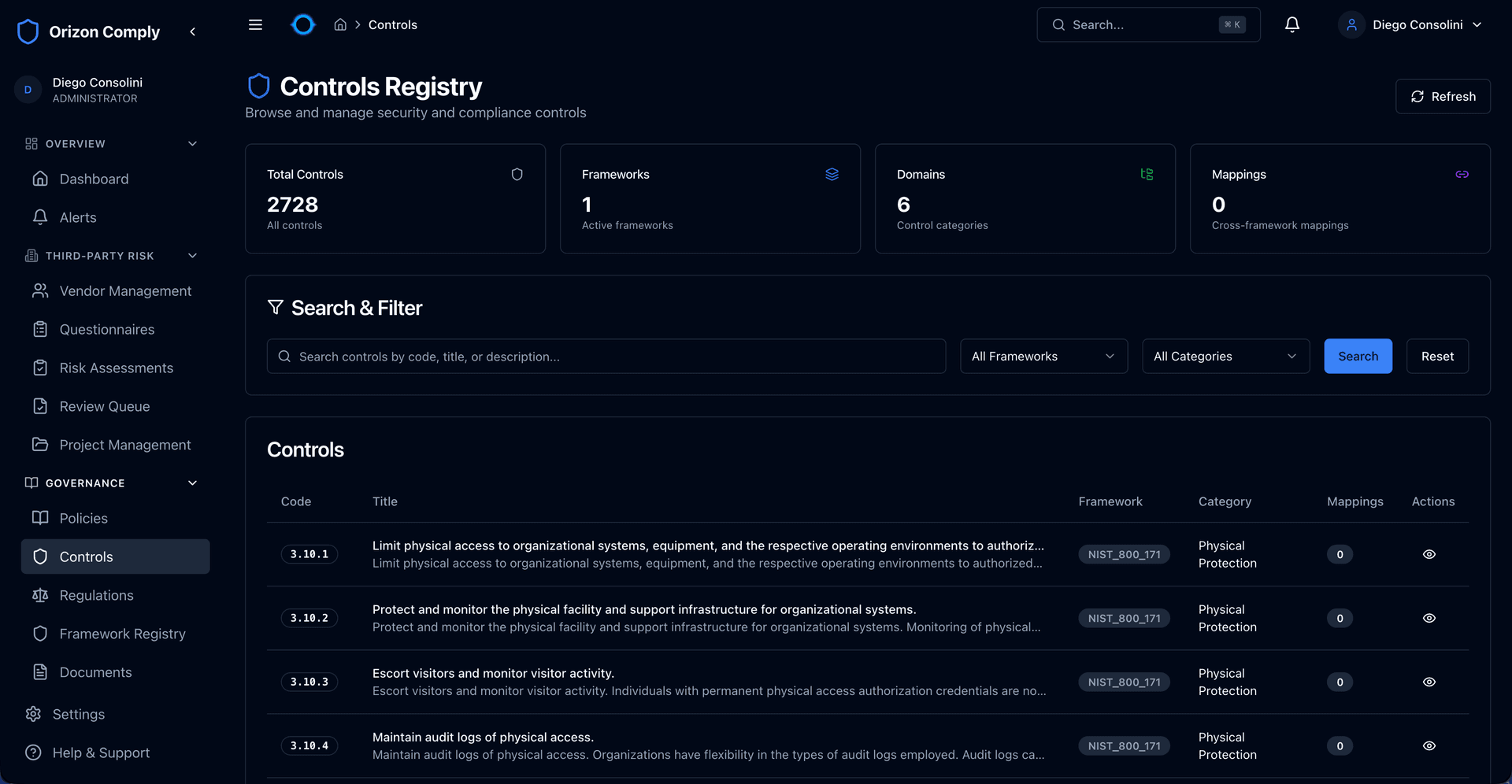
Controls Registry — searchable with framework and domain filters
OSCAL 1.0+
All 7 document types — Catalog, Profile, Component Definition, SSP, Assessment Plan, Results, POAM
CSA CCM v4
197 controls across 17 domains with CAIQ questionnaire
ISACA AI Audit
251 controls across 22 families with weighted risk scoring
GDPR
30 articles, 62 requirements with per-vendor tracking
DORA
Digital operational resilience for financial entities
MiCA
Crypto-asset regulation with compliance tracking
NIS2
Network security directive with article-level mapping
Cross-mapped to: NIST 800-53 · NIST CSF 2.0 · ISO 27001:2022 · PCI-DSS v4.0 · CIS v8 · SOC 2 TSC
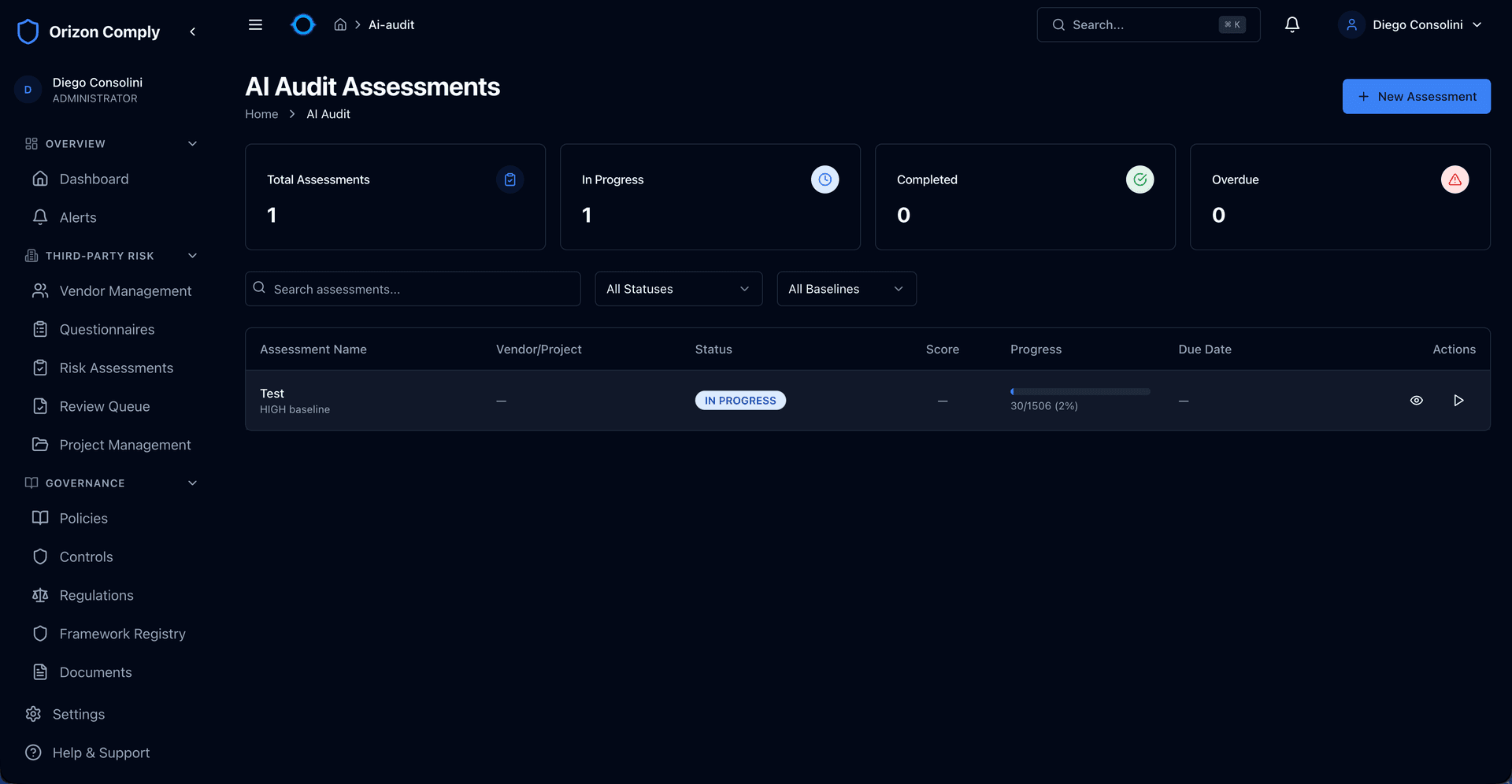
Privacy-First AI
Run AI-powered compliance audits using Ollama, WebLLM, and Transformers.js — all processing happens on your infrastructure. No data is sent to external LLMs, making it suitable for financial services, healthcare, and government environments.
Your compliance data never leaves your environment.
All AI processing runs locally — no external API calls, no data transfer, no third-party dependencies.
No vague claims. Every security control is specific, measurable, and auditable. Here is exactly what protects your data.
5 distinct roles — Administrator, Project Manager, Risk Analyst, Vendor Manager, Read-Only — with fine-grained permissions across 12+ resource types and 10+ action types.
Cryptographic session tokens with configurable IP binding (strict, warn, or off). Last-admin deletion prevention and 24-hour expiring email verification tokens.
Keycloak SSO via OIDC with conditional fallback to credential-based authentication when SSO is not configured.
Environment-aware CSP headers, CORS origin validation, CSRF protection, IDOR prevention, and path traversal protection.
14 action types logged with IP address, user agent, and timestamps. Export in CSV or JSON for external review.
Clean npm audit, download rate limiting at 100/hour/user, file validation on uploads, and verified-domain email notifications.
Whether you are managing ten vendors or a thousand, Orizon Comply scales with your compliance programme.